Waterfall methodology
Waterfall methodology
Definition of Waterfall
Why this is used – advantages and disadvantages
In the scope of CompSci/cyber projects
Learning Activity 1
• Learners to:
– Work in your groups to research the Waterfall methodology, noting down the purpose of the approach, and outlining what happens in each of the phases (60 minutes).
– Discuss and write down through your collaborative platform how each phase in the Waterfall methodology fits into the scope of computing or cyber security projects (30 minutes).
• Tutor to:
– Provide one-to-one guidance and support to learners.
Tasks and activities in the Waterfall process
Recall from the 126ITSC module, the definition of the waterfall model.
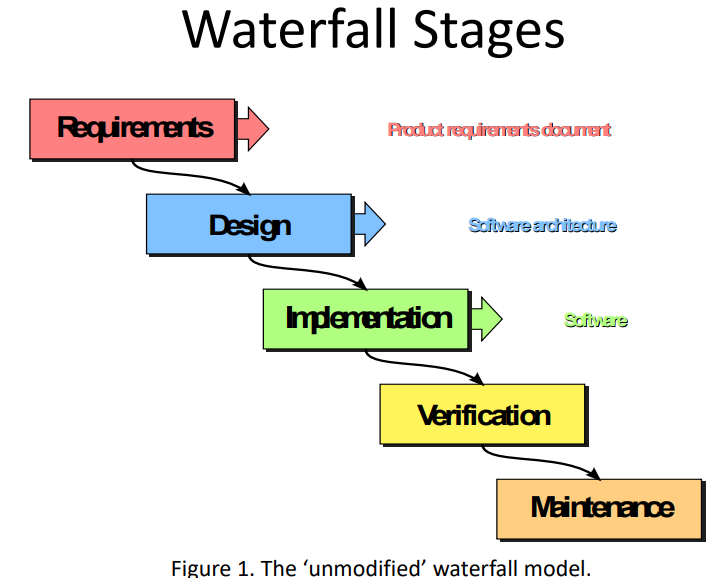
The waterfall model is a document-driven model with separate and distinct phases for specification and development. It tends to be among the less iterative and flexible approaches, as progress flows in largely one direction.
This is an example of a documentation-driven process where all of the process activities are planned in advance and progress is measured against this plan.
Waterfall Stages
• System and software requirements: captured in a product requirements document
• Analysis: resulting in models, schema, and business rules
• Design: resulting in the software architecture
• Coding: the development, proving, and integration of software
• Testing: the systematic discovery and debugging of defects
• Operations: the installation, migration, support, and maintenance of complete systems
Learning Activity 2
• Learners to:
– Work in your groups to discuss how the stages of the Waterfall methodology can be applied to your project. Note down and justify how each stage does/doesn’t meet your specific project and scope (90 minutes).
• Tutor to:
– Provide one-to-one guidance and support to learners.